
From the above image, you can see Wscript.exe writing a .JS file. This may be a good item to key in on as well. Again, some minot false positive may exist, but those should be easy to negate.

To This:

right away we can see that some data about the victim is being collected. In the following screenshot we will see the JS code and the resulting network traffic.
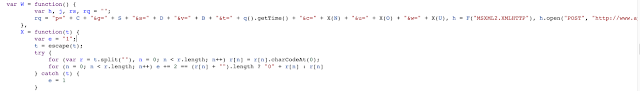


Based on this we can see the attempted POST data. Simple enough to decode. I'll focus on the "Computer Name, User Name and Windows Version"

As we already knew just by looking at the code, we can see and confirm that the network traffic is sending out data about our victim. I thought this was a fun exercise, so I wanted to share the POST data.
Third Detection Opportunity
Finally, I want to point out 1 additional detection opportunity that I've seen common with every JS/Bondat I've observed. Look for changes to the registry key path HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\
With changes to the registry key values of Hidden and ShowSuperHidden. Reference Screenshot below:

Again, you may have some false positive to rule out, perhaps you want to specify a parent process like wscript, or powershell or something from the %userprofile% path.
One final note, this worm spreads by copying itself to USB drives as well. An infected USB can then spread to each system its plugged into.


Comments
Post a Comment